DDoS Mitigation
SmartAdvantage℠
DDoS Mitigation Service
Our Team.
For more than 60 years, JSI has been a trusted advisor and preferred business partner to hundreds of independently owned communications providers across the United States. Today, we continue that tradition by offering our clients a comprehensive range of broadband solutions, including our SmartAdvantage℠ DDoS Mitigation subscription service, to help ensure their success – today, tomorrow, and in the decades ahead.
Our Service.
Since the rapid migration to remote access for students and employees, large-scale distributed denial-of-service (DDoS) attacks have increased in frequency, intensity, and duration.
There has also been an ever-increasing number of small-scale DDoS attacks, which have disrupted networks and impacted customer experience, but for far shorter periods of time. That often means that those attacks end and their symptoms disappear before network engineers can identify the cause of the disruptions.
JSI’s SmartAdvantage℠ DDoS Mitigation subscription service is affordable, rapidly deployable, and requires no other internet service provider (ISP) systems to operate. Contact our team today for a 30-day free trial and consultation with one of our engineers to learn more.
Our DDoS Mitigation service’s core features include:
(1) An automated, cloud-based solution.
(2) Automatic detection of a DDoS attack against a subscriber and mitigation it before it can disrupt other ISP customers;
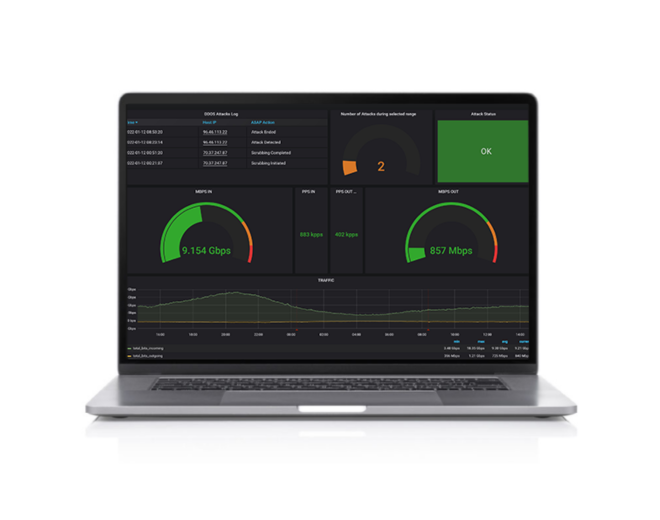
(3) An interactive, web-based tool, which you can use to see bandwidth consumption for any network IP.
(4) The ability to identify attacked IPs and to monitor the status of mitigation activities (only with standard and advanced plans).
With JSI’s DDoS Mitigation service, you and your company can have access to a range of critical tools and resources:
(1) Resources to monitor ISP traffic, including all upstream provider connections, for attacks before they reach the edge network.
(2) Robust mitigation solutions, which begin as soon as an attack is detected, either by terminating traffic to the targeted subscriber or filtering out attack traffic.
(3) The ability to filter out, or scrub, harmful DDoS traffic and pass on only legitimate subscriber traffic.
(4) Real-time or historical bandwidth graphing of when attacks occurred and targets for each of your IPs, subnets, or hole network.
For additional information on these services, simply click here to be connected with a senior member of our team.